Information Security Management System

Information Security Management System (ISMS)
Greenfiltec is dedicated to building a corporate culture that prioritizes information security, continuously improving our security governance to ensure business continuity and data protection. We set clear goals, implement security policies, and allocate resources to keep our measures up to date and effective.
一、Information and Communication Security Management Objectives
Ensure the confidentiality, integrity and availability of the company’s business and information, and protect customer privacy and information asset security.
二、Information and Communication Security Risk Management Framework
The IT department is responsible for information security in our company. It consists of one IT manager and one IT professional. The IT manager and professional also serve as the security officers, responsible for setting internal information security policies, planning and executing security measures, and promoting and implementing these policies. They regularly publish updates on the company’s security governance.
The Audit Office oversees information security supervision. It has an audit manager responsible for monitoring the internal execution of security measures. If any issues are found during audits, the audited unit is required to submit improvement plans and actions immediately. The Audit Office also regularly tracks progress to reduce internal security risks.
三、Information and Communication Security Policy
Our company is committed to building a corporate culture that highly values information security (ISMS) and actively improving our security governance to ensure business continuity and data safety. The information security team coordinates with various departments to promote and implement effective security management.
Our team follows the 「Plan-Do-Check-Action (PDCA)」cycle to review the relevance of security policies, continuously improving and tracking the effectiveness of protection measures. We regularly report to the audit department to ensure our security practices stay up to date and keep improving.
- Core Business System Security Management
- Information System Access Control
- Information Security Protection and Control Measures
- Information Security Risk Management and Incident Response Procedures
四、Specific Management Plans and Resource Allocation for Information and Communication Security
- User account registration and deactivation follow company user management policies, and accounts and permissions are regularly reviewed.
- The email system has filtering and malware detection to ensure secure email management.
- Annual disaster recovery drills are conducted to ensure the ability to respond to security incidents and reduce system operation risks.
- System servers are placed in restricted areas with controlled access.
- Regular information security awareness training is held each year to raise employees’ security awareness and understanding.
- Regular reports on information security implementation are made to the board of directors, with the latest report given on November 1, 2023.
- Threat intelligence gathering and security reporting are in place, and the company joined TWCERT/CC (Taiwan Computer Emergency Response Team/Coordination Center) in 2023.
- Security personnel attend relevant training courses every year to enhance their expertise and stay updated on key issues.
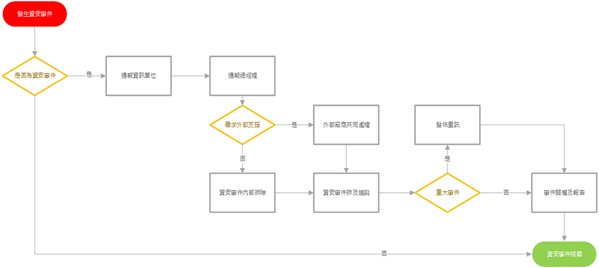
五、Information Security Incident Reporting Procedure
The company’s information security incident reporting procedure is as follows. All security incidents must be reported and handled according to this procedure.